Deep web networking

Ever since I was exposed to the deep web, I wondered how people hosted these sites. I used to find them very mysterious when I was younger, so sometime earlier this year (relative to when I'm writing this in 2020), I decided I was going to try to build one myself.
Mastermind is a deep website I pulled together using Tor Hidden Services that I keep running on a Raspberry Pi. Although the project is not yet finished, it has taught me a lot about server management and security; however, it also brought with it more questions than answers.
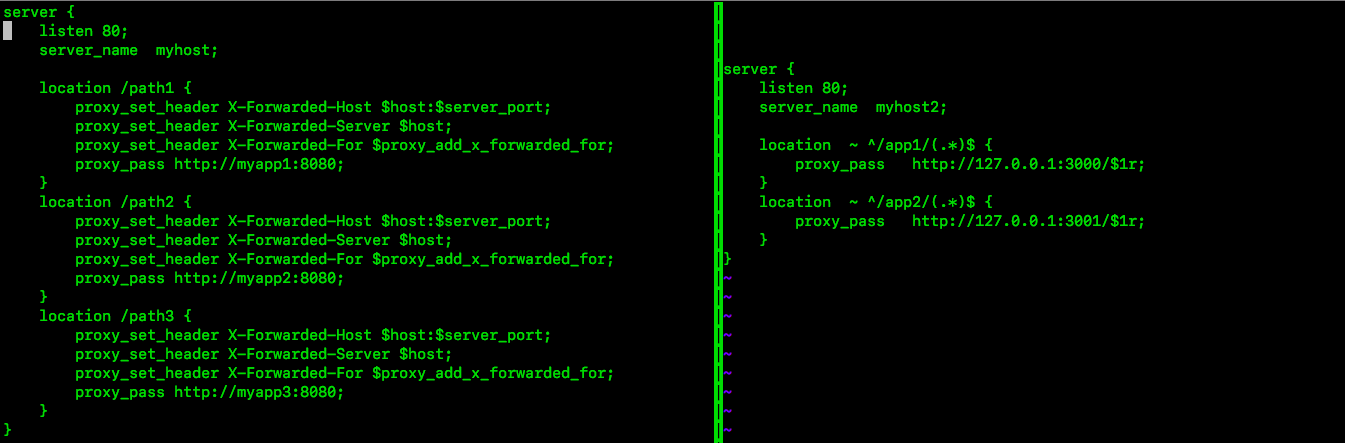
One of the first things I encountered was how to keep files from being public access. If you're familiar with the community on the deep web, there are plenty of hackers that roam from site-to-site looking for security exploits, so I needed to make sure my site abstained from showing unnecessary files. This is where I start learning about nginx. I also needed to learn a lot of CSS hacks, because I wouldn't be using JavaScript. Although some deep websites use JavaScript, it's typically frowned upon because it opens users up to security leaks. Revealing user information defeats the purpose of anonymity, so even if I implemented JavaScript, most users wouldn't enable it anyway.
Some clever CSS hacks I found were the carousel hack and the holy albatross. These tricks enable sites that are stripped of JavaScript to still have vitality. I enjoyed the challenge of keeping the aesthetic of the page satisfying with only CSS to style the contents.
Another problem I came across was differentiating v2 addresses with v3 addresses. This was something I was unfamiliar with when I was younger because it wasn't yet an issue, but as time progressed and hardware advanced there was need for higher security. The main issue was that v2 used 80 bit SHA1, meaning that modern computers could brute force their signatures and take control of the domain without much issue; whereas v3 addresses are longer and computationally more secure. If you want to read more on this, you can visit this page on the tor-project website.
From here, I started to question how people generated personalized tor links with custom substrings, give that the signatures generated are completely random; however, after researching for a short while I became familiar with the term "vanity address", which is a label for these customized addresses. The common method for retrieving these vanity addresses (in v3) is through brute-forcing keys and regexing the resulting addresses, which is where tools like mkp224o come in.
Although the website is not finished, the website has been deployed with tor hidden services and can be accessed through its v3 address. If you're interested in the website, I can supply it upon request; however, to avoid bot-surfing from retrieving my link, I would like to refrain from including it here on my portfolio. My futurue plans for this site include blogging, lightweight exploit documentation, and hardware schematics for legal hacking tools.