Quantum Hacking

Quantum cryptography has been an interest of mine ever since I heard about Shor's algorithm and its potential to break RSA encryption by allowing machines to factor out multiples of primes exponentially faster. Something that would take a classical supercomputer until the end of the universe would only take a quantum computer a year or two.
In addition to breaking RSA encryption, my brain started thinking about other things that quantum computers could break. One concept I thought of was teleporting data out of Wiesner's Quantum Currency. His quantum money scheme is a quantum cryptographic protocol to create and validate banknotes which are impossible to forge; however, that does not make them invulnerable to tampering. It's also fitting that quantum teleportation was discovered after the idea of quantum money was developed.

In Wiesner's quantum currency scheme, the number of digits in the serial correspond to the number of qubits in the register for the currency device.
The main benefit of Wiesner's quantum currency is that it's protected from copying because of the No-Cloning Theorem of quantum mechanics, which states that "it is impossible to create an independent and identical copy of an arbitrary unknown quantum state," which has profound implications in the field of quantum computing among others.
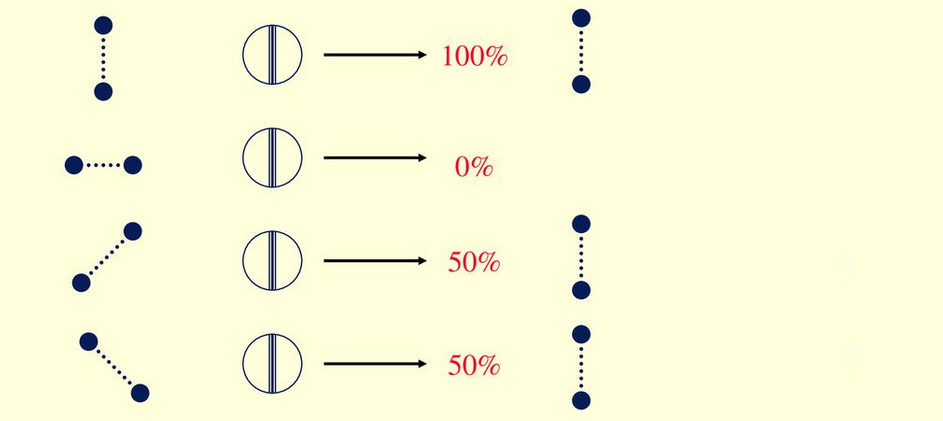
Wiesner's quantum currency would directly attack forgeries by making it highly unlikely for a counterfeit currency to make it into transit due to the nature of its quantum bits measured on a basis particular to its serial number and potentially a code known only by a bank; however, the latter creates its own issues.
As you may have guessed, if the bank is storing a code related to the serial information on the currency that also relates to its quantum nature, forgeries would be made easier if a hacker could retrieve that information. These bills would also be vulnerable to something called an Elitzur Vaidman Bomb attack, but they wouldn't make it very far if the bank didn't continually verify the note being taken. After verification, the bank should give a new bill to the customer to avoid counterfeiting.
Another idea I had was to somehow teleport information in and out of a piece of quantum currency. This can be done with the contemporary teleportation circuit, and it could be used for money laundering.
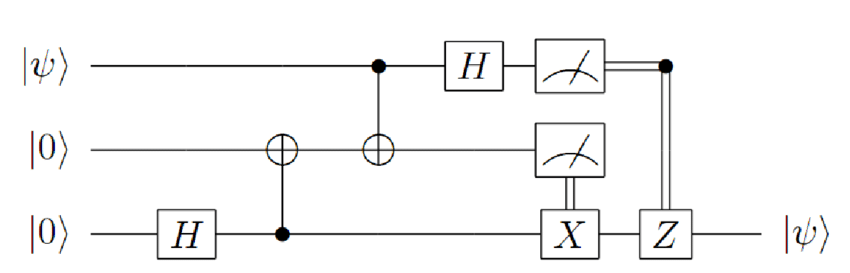
Essentially, the idea would be to iterate through all the qubits in a large dollar bill and teleport them into a one dollar bill. This would be done over several bills while maps are drawn between classical serial numbers to ensure counterfeits could be made later to smuggle large amounts of money securely.
Assuming we already have a secure quantum network, we can then use a quantum key algorithm to encrypt our messages on a classical channel to communicate our serial maps such that we can correctly and securely smuggle this money; however, an issue arises if anyone tries to spend these small dollar bills with the teleported quantum data encoded into them.
$$ 00 = \ket{0}, 01 = \ket{+}, 10 = \ket{-}, 11 = \ket{1} $$
So the general plan looks something like this:
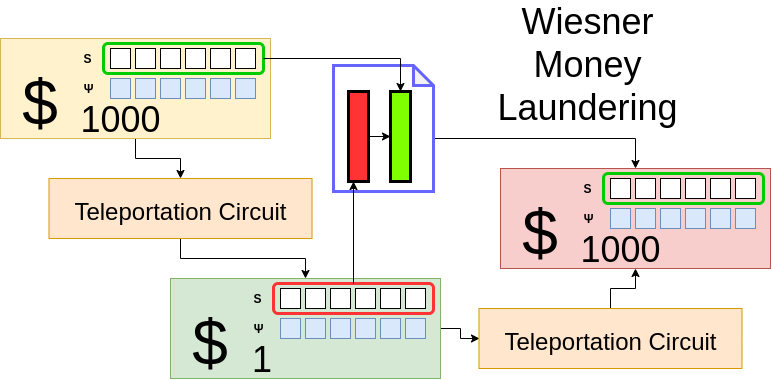
Basically the general process is to take the larger currency, teleport the qubits into a smaller currency, transport the smaller currency, teleport those qubits into a counterfeit bill, and then communicate the serial information for the serial over a secure channel. Given that the counterfeit is convincing, all the verifications should pass at any given bank.
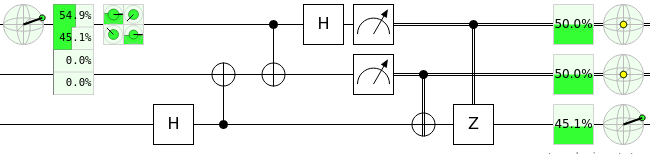
Another thing that got me thinking a lot was quantum spy detection. One of the things that makes this circuit really useful is its ability to detect spies with a level of certainty on a quantum network. I'll put two images by one another so you can see the difference between a regular quantum spy detector and one with a spy on the network.
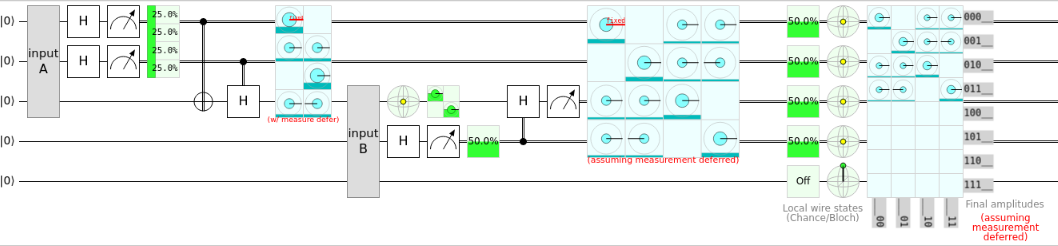
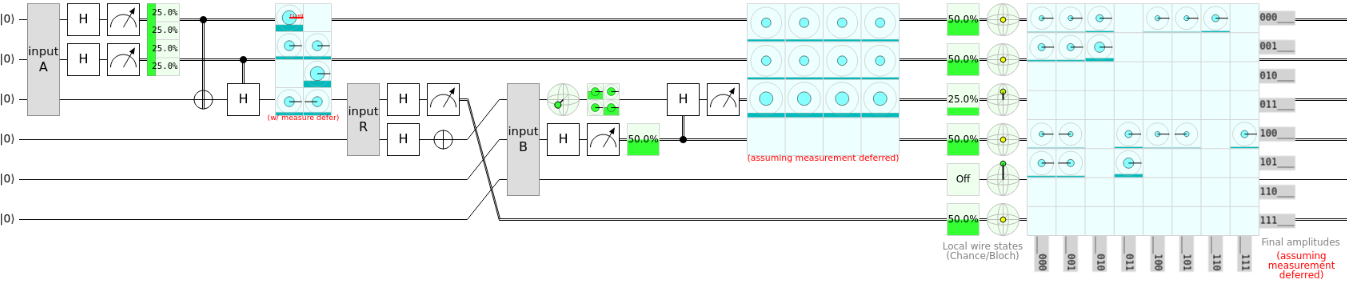
You can probably tell just by looking at the green bars that the probabilities are different between the spy and the lack there of; therefore, we can use these probability difference to infer over several iterations if there is a spy on the network. To me, this is quite possibly one of the coolest things developed in quantum computing aside from Shor's algorithm. After sharing the classical information that resulted in the outcome of the spy bit, we can assume the likelihood that a spy has taken over the network. This would have been useeful in the early 2000's when our privacy was still battling with the NSA.
However, if a spy gained access to the network, even if they didn't have a desire to access the data being transmitted, they could still trade their anonymity to fulfill a DoS (Denial of Service) attack and continually measure out the data being transmitted over the quantum network.
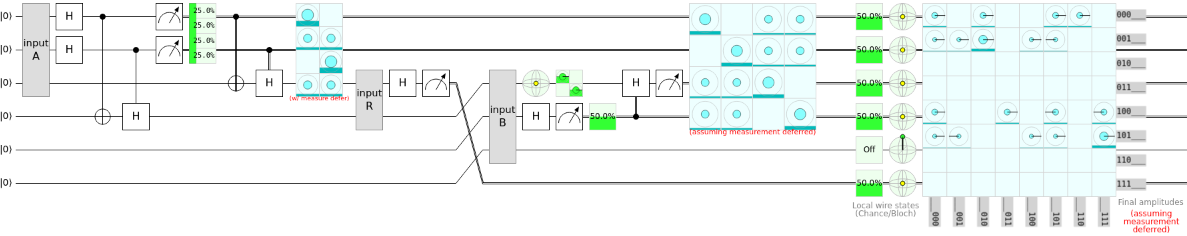
A possible attack on this spy detection circuit would be if the spy could gain access to the sender's machine and entangle their set of qubits with the sender's qubits such that they could determine the gates that would be applied to the spy detection qubit. This would be an advanced attack, but it would keep the spy from being detected one-hundred percent of the time (assuming that there is no noticeable quantum decoherence on the network sending false-positives).
This would enable both the sender and the spy to receive the random binary classical bits derived from measuring out a zero passed through Hadamard. This would completely defeat the spy detection technique discussed earlier; however, they would have to find a way to entangle these qubits for each iteration, which would be a very intrusive and difficult active reconaissance attack to perform.
Quantum hacking is an evolving, but promising, field that will likely yield a lot of interesting results. I firmly believe that one day the internet will flourish with open-source quantum exploits that developers come up with. Quantum algorithms will become one of the main bases of discovery as well as a fundamental for encryption and communication, making quantum hacking more desirable for those interested.